[Jenkins]Jenkins集群搭建, HTTPS和LDAP集成
![[Jenkins]Jenkins集群搭建, HTTPS和LDAP集成](/content/images/size/w1200/2020/08/logo-title-opengraph.png)
接到需求,要搭建一个新的Jenkins集群,需要:
- 1 Master with 2 Slaves
- HTTPS
- LDAP集成
- 运行SAST,DAST管线
- 更换Jenkins Home Directory(后续发现的需求)
Mirror遇到一点问题
系统用的是RHEL7/CentOS7
搭建Master Server
HTTPS连接
网络团队设置Load Balancer指向了Master Server, 并且做了SSL offload, 所以指向LB Port 443的traffic会decode SSL然后送去Server的Port 80。这种情况下,我们只要让Jenkins在Port 80跑就可以了。
- Ensure that iptables has allowed traffic on port 80 and 8080.
iptables -L -n
你可能会看到如下规则
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8080
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8443
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
- 如果没有,运行如下命令添加port,比如80
sudo iptables -I INPUT 1 -p tcp --dport 80 -j ACCEPT
- Forward port 80 traffic to 8080
sudo iptables -A PREROUTING -t nat -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 8080
- 可以使用
iptables -L -t nat来检测
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
REDIRECT tcp -- anywhere anywhere tcp dpt:http redir ports 8080
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
- 保存iptables configuration到系统
sudo iptables-save > /etc/sysconfig/iptables
LDAP集成
- 安装SAML插件
- Manage Jenkins-->Security:Configure Global Security
- 设置LDAP Server和参数,此处参考了旧集群的配置
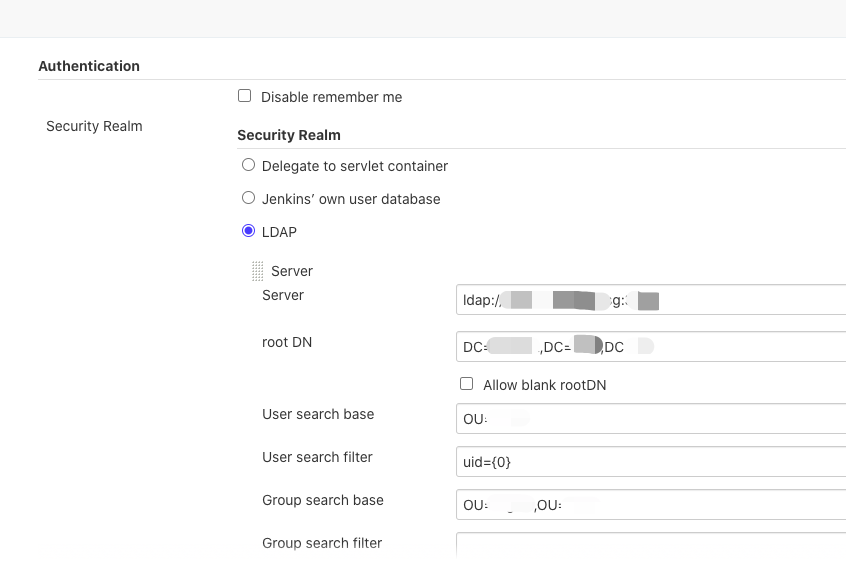
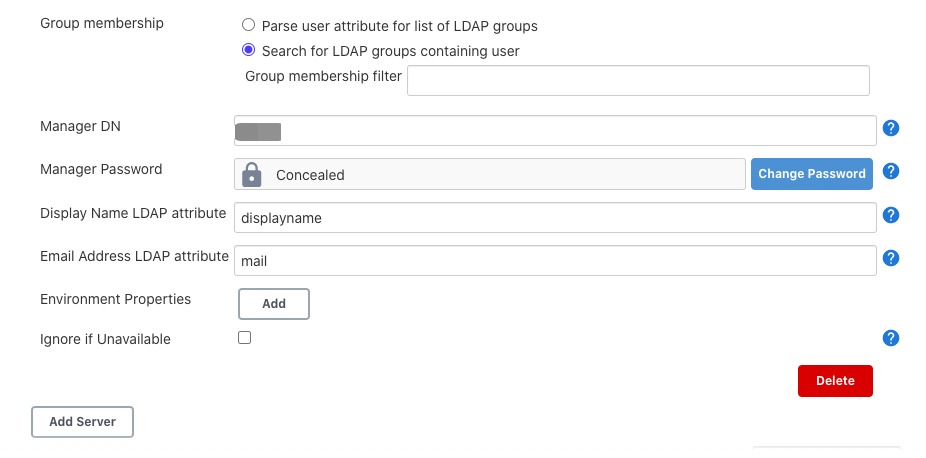
5. 添加Manager DN和Manager Password, 用来先向LDAP服务器authenticatre自身。
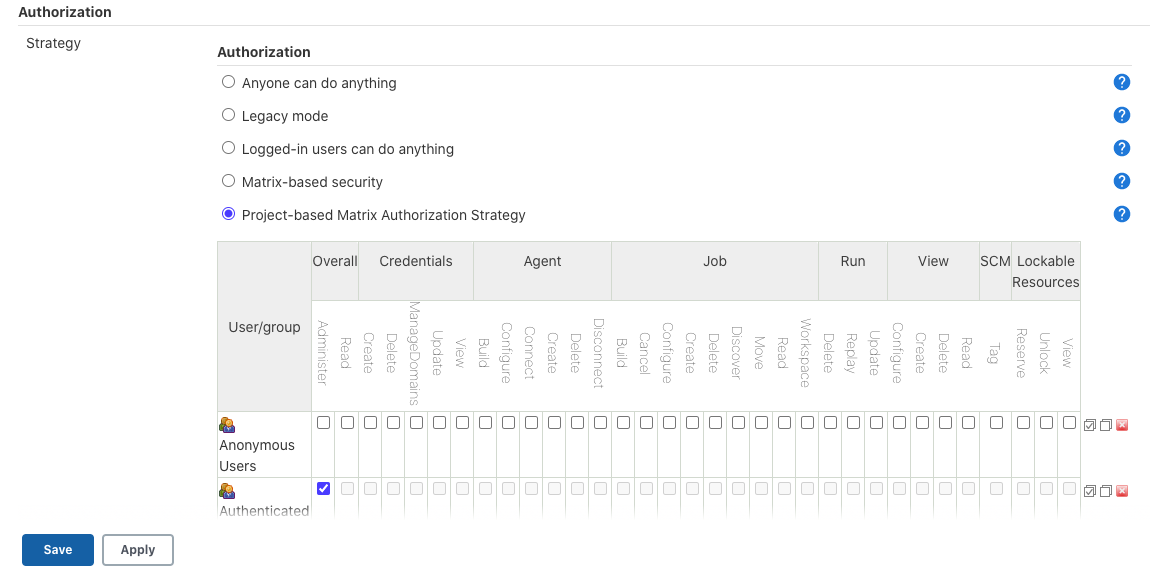
5. 使用Project based matrix管理权限
更换Jenkins Home Directory
后来发现硬盘太小,想重新挪动个地方,于是需要迁徙Jenkins到新的目录。
- 确认旧的(默认)目录在/var/lib/jenkins。可以在Manage Jenkins-->System Information里Environment Variables的HOME里查看。
- 停止服务:
sudo service jenkins stop - 新建目录并chown给予目录权限
mkdir /static/jenkins
sudo chown jenkins:jenkins /static/jenkins
- 拷贝旧目录里的内容到新目录:
sudo cp -prv /var/lib/jenkins /static/jenkins/ - 更改Jenkins user home:
sudo usermod -d /static/jenkins/ jenkins - 在配置文件里更新Jenkins home directory。对RHEL/CentOS来说,是/etc/sysconfig/jenkins:
# jenkins home location
JENKINS_HOME=/home/new_home
- 重启服务:
sudo service jenkins start - 拷贝新密码用来在UI解锁Jenkins:
cat /static/jenkins/secrets/initialAdminPassword - 最后重新在老途径确认HOME变量,Manage Jenkins-->System Information-->Environment Variables-->HOME。
Slave的链接
在连接slave的初期遇到一些问题,主要是ssh refuse。
[SSH] Authentication Failed
Authentication failed.
Launch failed - cleaning up connection
[SSH] Connection closed.
考虑到几台服务器的/static都mount去了同一个nfs, 决定在/static里分别生成slave directory用来做slave machine的jenkins home。
[root@appsec-jenkins-s112 static]# ls
jenkins jenkins_slave
[root@appsec-jenkins-s112 static]# ls jenkins_slave/
appsec-jenkins-s111 appsec-jenkins-s112
[root@appsec-jenkins-s112 static]#
在/etc/passwd里添加jenkins用户,和对应的Home directory(如果没有对应的jenkins用户)
jenkins:x:164:117:Jenkins Automation Server:/static/jenkins:/bin/bash
和添加group(从老服务器里grep然后写入/etc/group):grep jenkins /etc/group
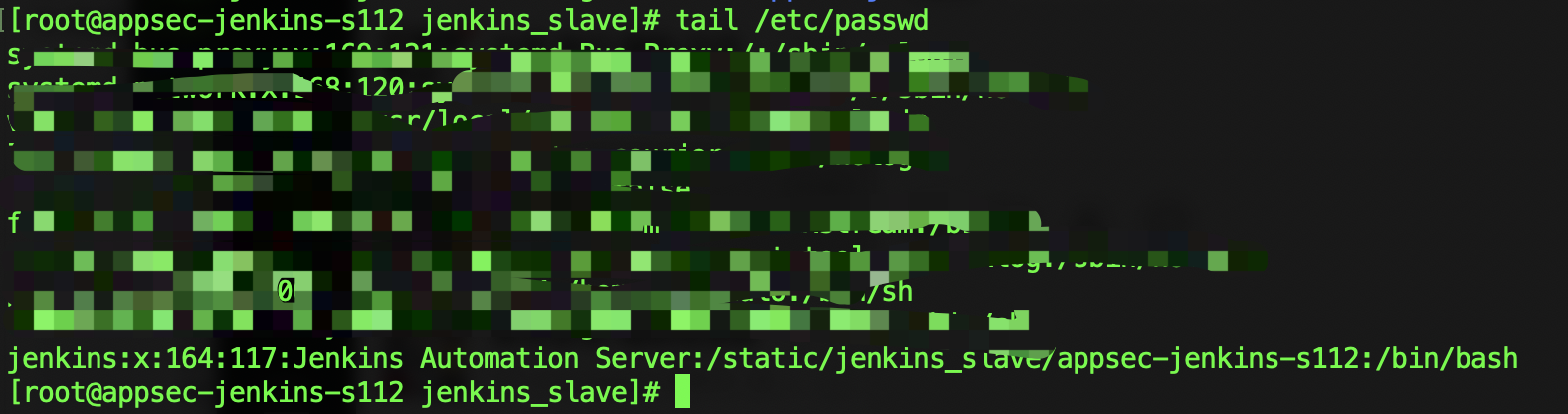
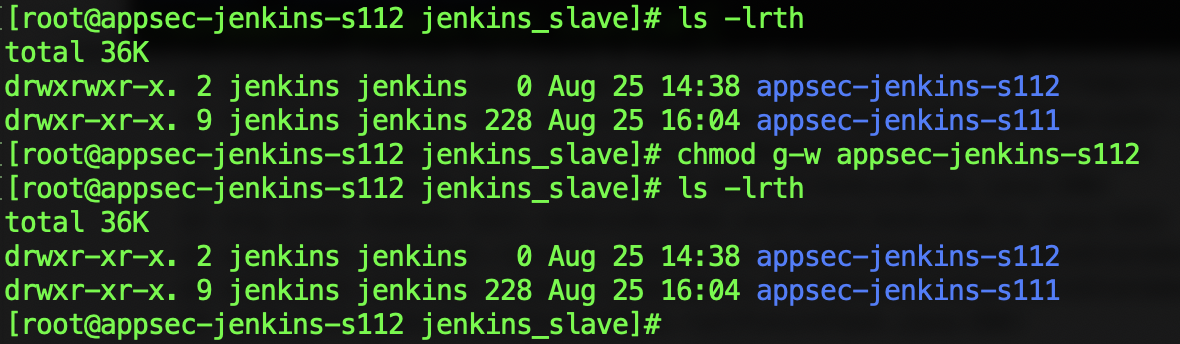
chown -R jenkins:jenkins /static/jenkins_slave/appsec-jenkins-s112
usermod -d /static/jenkins_slave/appsec-jenkins-s112 jenkins
chmod g-w appsec-jenkins-s112
这里需要注意的是,要去除home directory的group权限 才可以sshkey登录,小踩了个坑。
在Master生成ssh key pair:ssh-keygen -t rsa -C "The access key for Jenkins slaves"
在slave服务器,jenkins的home directory: ~/.ssh/authorized_keys里添加public key, 在master的credential里放入private key。
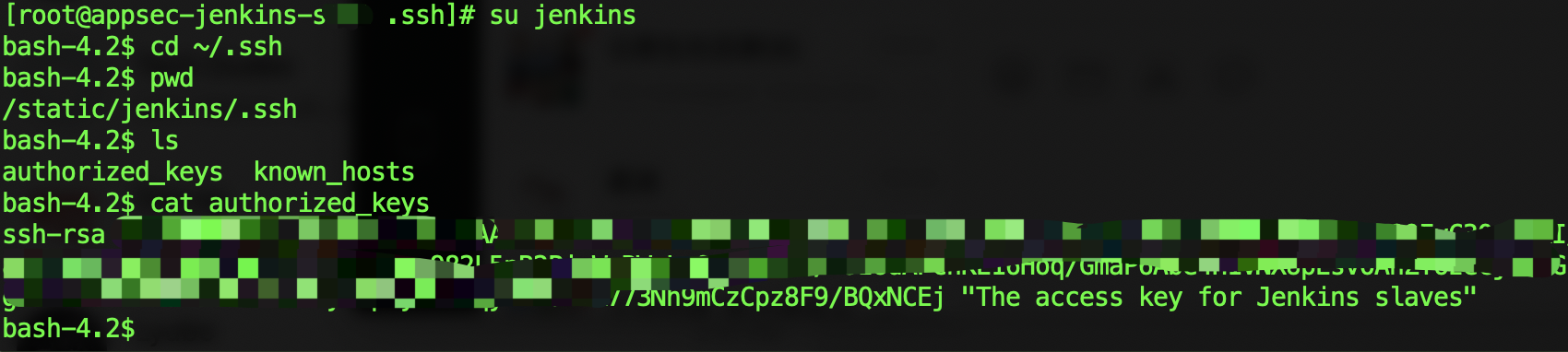
把key的权限改成600
[root@appsec-jenkins-s112 .ssh]# ls -lrth
total 26K
-rw-r--r--. 1 root jenkins 417 Aug 25 18:17 authorized_keys
[root@appsec-jenkins-s112 .ssh]# chown jenkins:jenkins authorized_keys
[root@appsec-jenkins-s112 .ssh]# chmod 600 authorized_keys
[root@appsec-jenkins-s112 .ssh]# ls -lrth
total 26K
-rw-------. 1 jenkins jenkins 417 Aug 25 18:17 authorized_keys
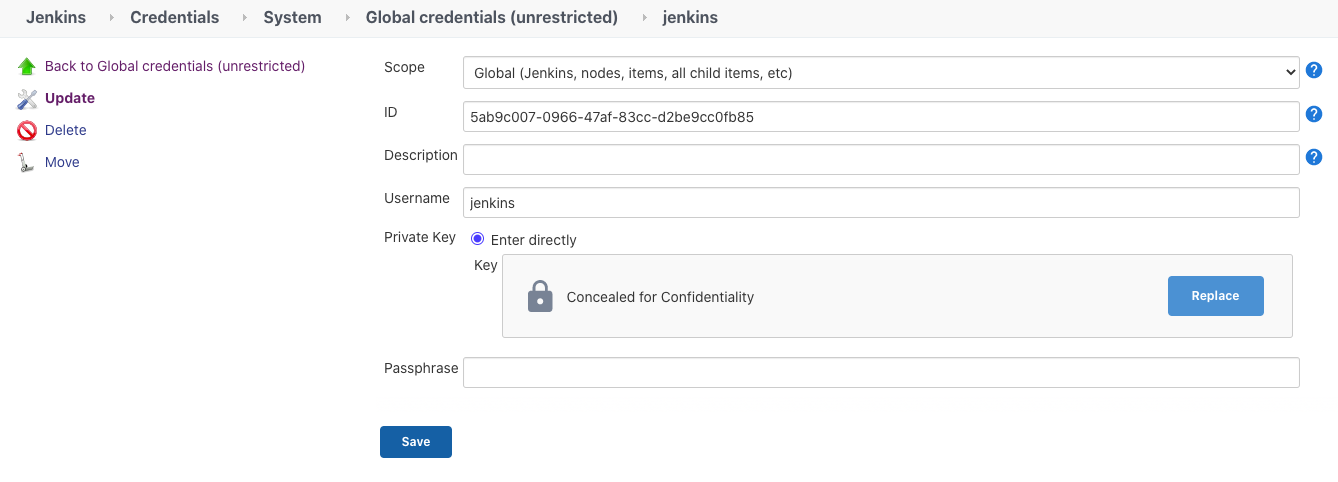
chown jenkins:jenkins -R /static/jenkins
先测试从Master用ssh key登录Slave.
去除home directory的group权限 才可以sshkey登录
ssh -i id_rsa jenkins@appsec-jenkins-s112.xxxxx.yyyyy.com.sg -p5722
这下就连上啦~
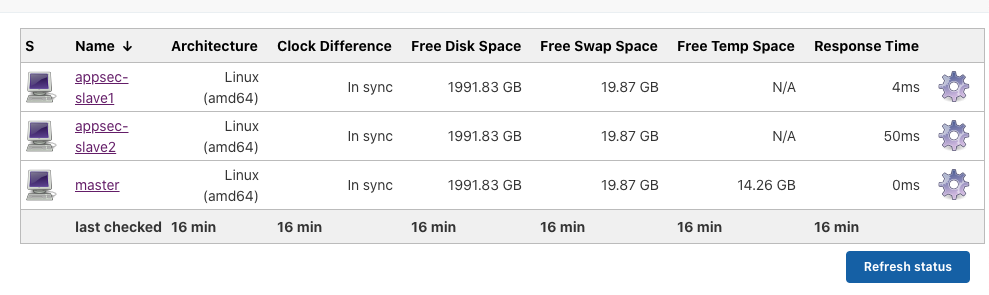
但是运行pipeline时似乎又遇到了其他的问题:
FATAL: Unable to produce a script file
java.io.IOException: No such file or directory
at java.io.UnixFileSystem.createFileExclusively(Native Method)
at java.io.File.createTempFile(File.java:2026)
at hudson.FilePath$CreateTextTempFile.invoke(FilePath.java:1470)
记得添加/tmp, JVM Option
最后又遇到幺蛾子 写入不了tmp 重启服务器后解决.
采坑:SSH refused
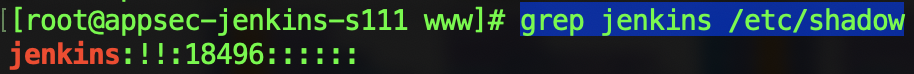
由于手动添加jenkins账号时只照猫画虎了/etc/passwd却漏了/etc/shadow, 导致可以本地su, 却无法远程登录。通过添加/etc/shadow中jenkins记录解决。相关知识点请移步这篇Linux中的/etc/passwd和/etc/shadow。
[root@appsec-jenkins-s111 www]# grep jenkins /etc/shadow
jenkins:!!:18496::::::
又踩了个坑:重启后无法ssh远程登录
我们的服务器默认不使用iptables。在本文第一部分prerouting前添加了Chain INPUT(policy ACCEPT), 导致重启后iptables block了其他端口,包括SSH。
解决方法是iptables --flush
之后会另写一篇关于iptables的新日志以作知识补充。
https://blog.csdn.net/weixin_30588827/article/details/101425330
https://wangchujiang.com/linux-command/c/iptables.html
References:
https://wiki.jenkins.io/display/JENKINS/Running+Jenkins+on+Port+80+or+443+using+iptables
https://dzone.com/articles/jenkins-02-changing-home-directory
https://devopscube.com/setup-slaves-on-jenkins-2/
https://kinsta.com/knowledgebase/ssh-connection-refused/
http://www.chinastor.com/os/linux/092034W22016.html
https://blog.csdn.net/yaofeiNO1/article/details/54616440